HACKER MACHINES, MY OWN CTF
Hi, everyone!
I’m very excited to share an exciting cybersecurity challenge with you. As you can see from the title, it’s a CTF (Capture The Flag) that I have developed. The goal of this challenge is to prove your skills and work on improving your knowledge in this fascinating field.
This CTF is composed of several challenges, each of which will test your abilities in finding vulnerabilities and overcoming obstacles to uncover the flag. The challenges have different rates of difficulty and will require a lot of skills and approaches to resolve. It doesn’t matter if you are a beginner or an expert; you are welcome to participate!
To join, you need to follow the link above, where you will find the instructions that explain how to set up the Virtual Machine to solve the challenges.
I’m very grateful to see how you tackle this CTF and share your knowledge with the community. Don’t hesitate to share your achievements, questions, or discoveries when you are resolving the CTF. Good luck and enjoy!
Click here to download the CTF.
CTF Description
This project is based on the use of Oracle VirtualBox, widely used virtualization software, to create a virtual machine with the Ubuntu 22.04 operating system. Within this virtual machine, services and applications are configured to simulate a real environment with various vulnerabilities.
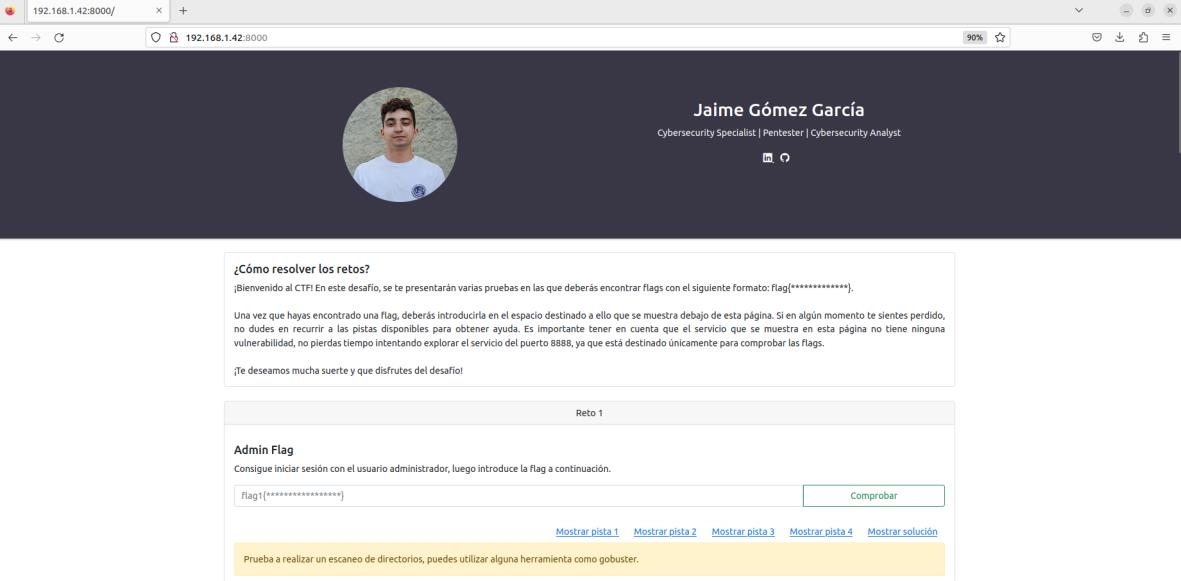
The main objective is to provide a secure and controlled environment in which participants can test their cybersecurity skills. To achieve this, an HTTP service is deployed on port 8000 of the virtual machine. This service serves as the stage for the challenges that participants will face, as seen in Figure 3.1.
Each challenge is presented as a specific problem or vulnerability that participants must identify and exploit to obtain a “flag” (a unique text string representing success in solving the challenge). As participants progress in solving the challenges, they can find hints and solutions on the deployed HTTP service. This helps them understand the existing vulnerabilities and learn the necessary techniques to exploit them ethically.
In addition to challenges and hints, there are input fields where participants can enter the flags they have discovered. This allows them to demonstrate that they have successfully overcome each challenge and advance in the CTF competition.
Theme of the Challenges
To give challenges a theme, a platform developed by the university professor has been simulated. Its purpose is to provide students with interactive access to various virtual laboratories where they can face challenges and solve problems related to different areas of study.
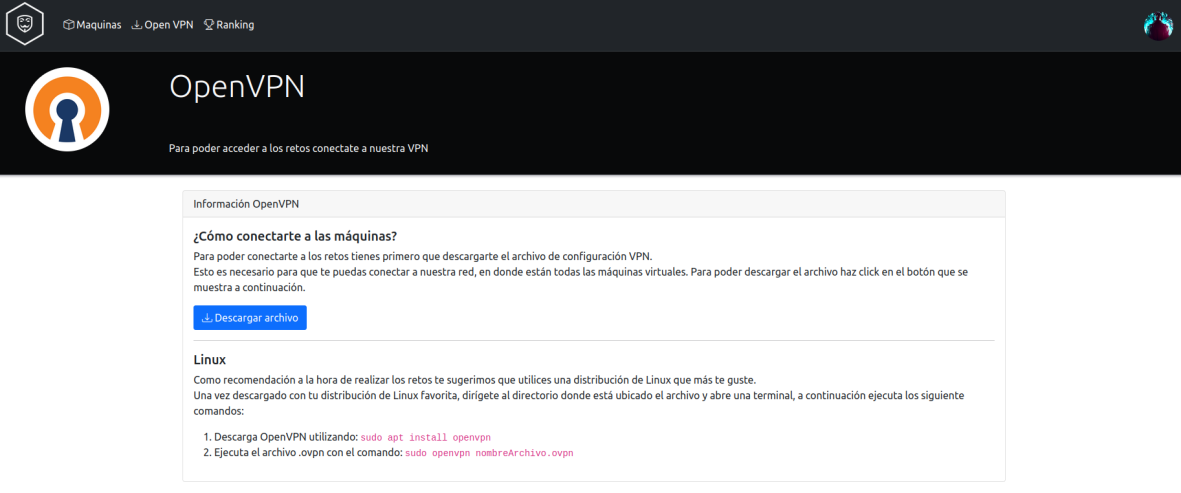
Through this platform, students will have the opportunity to immerse themselves in specially configured virtual environments with challenges and puzzles designed to test their knowledge and skills. To access these virtual laboratories, students will need to establish a connection using the OpenVPN protocol, as shown in the following image.
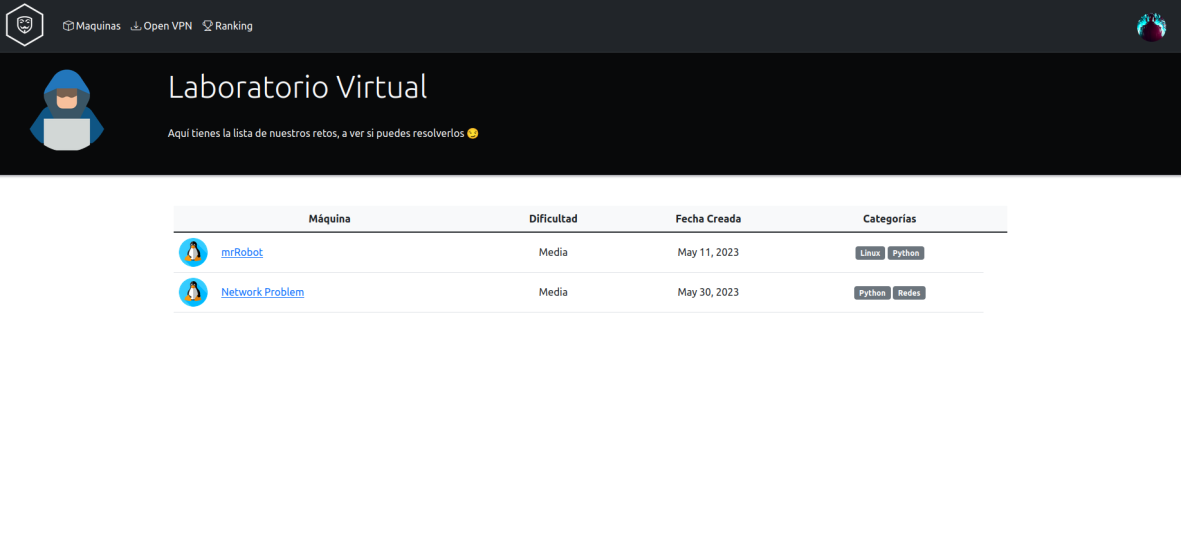
Each virtual laboratory will present real-world scenarios, simulating situations and problems that students may encounter in their future professions. These challenges will cover various disciplines, such as computer security, networking, programming, operating systems, and more, providing students with the opportunity to apply and develop their skills in a practical and controlled environment.